Profile-based and customizable assessments

Based on predefined Profiles
A type of assessment that allows you to take advantage of dynamic assessment suites without having to select categories. Our experts have prepared ready-made profiles corresponding to the most popular job positions in IT. Each profile is a combination of various categories appropriate to a given job position, based on which the platform generates unique assessment. All questions are scored automatically and the user who orders the assessment sees a detailed final report.
High quality content
Thoughtfully prepared by our experts.
Full automation
To save your money and time.
Convenient workflow
Just a few steps to achieve your goals.
Predefined Profiles prepared by experts
Covering most popular job positions.
Low cost
To avoid draining your budget.
Detailed report with summary
For an overview or details.

Based on custom Profiles
A solution based on our huge database of questions divided into specific categories. The user selects the categories he is interested in and the number of questions in these categories, and the platform creates a unique set of questions. This approach works well both in the case of positions that combine different responsibilities as well as when the user wants to have control over which areas of knowledge are to be verified during the assessment. All questions are scored automatically and the user who orders the assessment sees a detailed final report.
High quality content
Thoughtfully prepared by our experts.
Full automation
To save your money and time.
Convenient workflow
Just a few steps to achieve your goals.
Flexible topics combination according to your needs
To tailor the assessment to your needs.
Low cost
To avoid draining your budget.
Detailed report with summary
For an overview or details.
All Profiles
The assessment profiles we have created were built for the most popular IT job positions found in companies around the world. Each profile covers multiple topics that are closely related to a given position. The profiles were created as a result of content analyzes of hundreds of job advertisements and improved using our extensive practical experience with technology. If you think that any additional profile should appear on this list, please let us know!
Proficiency level: Entry
Category configuration:
Proficiency level: Regular
Category configuration:
Proficiency level: Senior
Category configuration:
Proficiency level: Entry
Category configuration:
Proficiency level: Regular
Category configuration:
Proficiency level: Senior
Category configuration:
Proficiency level: Entry
Category configuration:
Proficiency level: Regular
Category configuration:
Proficiency level: Senior
Category configuration:
Proficiency level: Entry
Category configuration:
Proficiency level: Regular
Category configuration:
Proficiency level: Senior
Category configuration:
Proficiency level: Entry
Category configuration:
Proficiency level: Regular
Category configuration:
Proficiency level: Senior
Category configuration:
Proficiency level: Entry
Category configuration:
Proficiency level: Regular
Category configuration:
Proficiency level: Senior
Category configuration:
Proficiency level: Entry
Category configuration:
Proficiency level: Regular
Category configuration:
Proficiency level: Senior
Category configuration:
Proficiency level: Entry
Category configuration:
Proficiency level: Regular
Category configuration:
Proficiency level: Senior
Category configuration:
Proficiency level: Entry
Category configuration:
Proficiency level: Regular
Category configuration:
Proficiency level: Senior
Category configuration:
Proficiency level: Entry
Category configuration:
Proficiency level: Regular
Category configuration:
Proficiency level: Senior
Category configuration:
Proficiency level: Entry
Category configuration:
Proficiency level: Regular
Category configuration:
Proficiency level: Senior
Category configuration:
Proficiency level: Entry
Category configuration:
Proficiency level: Regular
Category configuration:
Proficiency level: Senior
Category configuration:
Proficiency level: Entry
Category configuration:
Proficiency level: Regular
Category configuration:
Proficiency level: Senior
Category configuration:
Proficiency level: Entry
Category configuration:
Proficiency level: Regular
Category configuration:
Proficiency level: Senior
Category configuration:
Proficiency level: Entry
Category configuration:
Proficiency level: Regular
Category configuration:
Proficiency level: Senior
Category configuration:
Proficiency level: Entry
Category configuration:
Proficiency level: Regular
Category configuration:
Proficiency level: Senior
Category configuration:
Proficiency level: Entry
Category configuration:
Proficiency level: Regular
Category configuration:
Proficiency level: Senior
Category configuration:
Proficiency level: Entry
Category configuration:
Proficiency level: Regular
Category configuration:
Proficiency level: Senior
Category configuration:
Proficiency level: Entry
Category configuration:
Proficiency level: Regular
Category configuration:
Proficiency level: Senior
Category configuration:
Proficiency level: Entry
Category configuration:
Proficiency level: Regular
Category configuration:
Proficiency level: Senior
Category configuration:
Proficiency level: Entry
Category configuration:
Proficiency level: Regular
Category configuration:
Proficiency level: Senior
Category configuration:
Proficiency level: Entry
Category configuration:
Proficiency level: Regular
Category configuration:
Proficiency level: Senior
Category configuration:
Proficiency level: Entry
Category configuration:
Proficiency level: Regular
Category configuration:
Proficiency level: Senior
Category configuration:
Proficiency level: Entry
Category configuration:
Proficiency level: Regular
Category configuration:
Proficiency level: Senior
Category configuration:
Proficiency level: Entry
Category configuration:
Proficiency level: Regular
Category configuration:
Proficiency level: Senior
Category configuration:
Proficiency level: Entry
Category configuration:
Proficiency level: Regular
Category configuration:
Proficiency level: Senior
Category configuration:
Proficiency level: Entry
Category configuration:
Proficiency level: Regular
Category configuration:
Proficiency level: Senior
Category configuration:
Proficiency level: Entry
Category configuration:
Proficiency level: Regular
Category configuration:
Proficiency level: Senior
Category configuration:
Proficiency level: Entry
Category configuration:
Proficiency level: Regular
Category configuration:
Proficiency level: Senior
Category configuration:
Proficiency level: Entry
Category configuration:
Proficiency level: Regular
Category configuration:
Proficiency level: Senior
Category configuration:
Proficiency level: Entry
Category configuration:
Proficiency level: Regular
Category configuration:
Proficiency level: Senior
Category configuration:
Proficiency level: Entry
Category configuration:
Proficiency level: Regular
Category configuration:
Proficiency level: Senior
Category configuration:
Proficiency level: Entry
Category configuration:
Proficiency level: Regular
Category configuration:
Proficiency level: Senior
Category configuration:
Proficiency level: Entry
Category configuration:
Proficiency level: Regular
Category configuration:
Proficiency level: Senior
Category configuration:
Proficiency level: Entry
Category configuration:
Proficiency level: Regular
Category configuration:
Proficiency level: Senior
Category configuration:
Proficiency level: Entry
Category configuration:
Proficiency level: Regular
Category configuration:
Proficiency level: Senior
Category configuration:
Proficiency level: Entry
Category configuration:
Proficiency level: Regular
Category configuration:
Proficiency level: Senior
Category configuration:
Proficiency level: Entry
Category configuration:
Proficiency level: Regular
Category configuration:
Proficiency level: Senior
Category configuration:
Proficiency level: Entry
Category configuration:
Proficiency level: Regular
Category configuration:
Proficiency level: Senior
Category configuration:
Proficiency level: Entry
Category configuration:
Proficiency level: Regular
Category configuration:
Proficiency level: Senior
Category configuration:
Proficiency level: Entry
Category configuration:
Proficiency level: Regular
Category configuration:
Proficiency level: Senior
Category configuration:
Proficiency level: Entry
Category configuration:
Proficiency level: Regular
Category configuration:
Proficiency level: Senior
Category configuration:
Proficiency level: Entry
Category configuration:
Proficiency level: Regular
Category configuration:
Proficiency level: Senior
Category configuration:
Proficiency level: Entry
Category configuration:
Proficiency level: Regular
Category configuration:
Proficiency level: Senior
Category configuration:
Proficiency level: Entry
Category configuration:
Proficiency level: Regular
Category configuration:
Proficiency level: Senior
Category configuration:
Proficiency level: Entry
Category configuration:
Proficiency level: Regular
Category configuration:
Proficiency level: Senior
Category configuration:
Proficiency level: Entry
Category configuration:
Proficiency level: Regular
Category configuration:
Proficiency level: Senior
Category configuration:
Proficiency level: Entry
Category configuration:
Proficiency level: Regular
Category configuration:
Proficiency level: Senior
Category configuration:
Proficiency level: Entry
Category configuration:
Proficiency level: Regular
Category configuration:
Proficiency level: Senior
Category configuration:
Proficiency level: Entry
Category configuration:
Proficiency level: Regular
Category configuration:
Proficiency level: Senior
Category configuration:
Proficiency level: Entry
Category configuration:
Proficiency level: Regular
Category configuration:
Proficiency level: Senior
Category configuration:
Proficiency level: Entry
Category configuration:
Proficiency level: Regular
Category configuration:
Proficiency level: Senior
Category configuration:
Proficiency level: Entry
Category configuration:
Proficiency level: Regular
Category configuration:
Proficiency level: Senior
Category configuration:
Proficiency level: Entry
Category configuration:
Proficiency level: Regular
Category configuration:
Proficiency level: Senior
Category configuration:
Proficiency level: Entry
Category configuration:
Proficiency level: Regular
Category configuration:
Proficiency level: Senior
Category configuration:
Proficiency level: Entry
Category configuration:
Proficiency level: Regular
Category configuration:
Proficiency level: Senior
Category configuration:
Proficiency level: Entry
Category configuration:
Proficiency level: Regular
Category configuration:
Proficiency level: Senior
Category configuration:
Proficiency level: Entry
Category configuration:
Proficiency level: Regular
Category configuration:
Proficiency level: Senior
Category configuration:
Proficiency level: Entry
Category configuration:
Proficiency level: Regular
Category configuration:
Proficiency level: Senior
Category configuration:
Proficiency level: Entry
Category configuration:
Proficiency level: Regular
Category configuration:
Proficiency level: Senior
Category configuration:
Proficiency level: Entry
Category configuration:
Proficiency level: Regular
Category configuration:
Proficiency level: Senior
Category configuration:
Proficiency level: Entry
Category configuration:
Proficiency level: Regular
Category configuration:
Proficiency level: Senior
Category configuration:
Proficiency level: Entry
Category configuration:
Proficiency level: Regular
Category configuration:
Proficiency level: Senior
Category configuration:
Proficiency level: Entry
Category configuration:
Proficiency level: Regular
Category configuration:
Proficiency level: Senior
Category configuration:
Proficiency level: Entry
Category configuration:
Proficiency level: Regular
Category configuration:
Proficiency level: Senior
Category configuration:
Proficiency level: Entry
Category configuration:
Proficiency level: Regular
Category configuration:
Proficiency level: Senior
Category configuration:
Proficiency level: Entry
Category configuration:
Proficiency level: Regular
Category configuration:
Proficiency level: Senior
Category configuration:
Proficiency level: Entry
Category configuration:
Proficiency level: Regular
Category configuration:
Proficiency level: Senior
Category configuration:
Proficiency level: Entry
Category configuration:
Proficiency level: Regular
Category configuration:
Proficiency level: Senior
Category configuration:
Proficiency level: Entry
Category configuration:
Proficiency level: Regular
Category configuration:
Proficiency level: Senior
Category configuration:
Proficiency level: Entry
Category configuration:
Proficiency level: Regular
Category configuration:
Proficiency level: Senior
Category configuration:
Proficiency level: Entry
Category configuration:
Proficiency level: Regular
Category configuration:
Proficiency level: Senior
Category configuration:
Proficiency level: Entry
Category configuration:
Proficiency level: Regular
Category configuration:
Proficiency level: Senior
Category configuration:
Proficiency level: Entry
Category configuration:
Proficiency level: Regular
Category configuration:
Proficiency level: Senior
Category configuration:
Proficiency level: Entry
Category configuration:
Proficiency level: Regular
Category configuration:
Proficiency level: Senior
Category configuration:
Proficiency level: Entry
Category configuration:
Proficiency level: Regular
Category configuration:
Proficiency level: Senior
Category configuration:
Proficiency level: Entry
Category configuration:
Proficiency level: Regular
Category configuration:
Proficiency level: Senior
Category configuration:
Proficiency level: Entry
Category configuration:
Proficiency level: Regular
Category configuration:
Proficiency level: Senior
Category configuration:
Proficiency level: Entry
Category configuration:
Proficiency level: Regular
Category configuration:
Proficiency level: Senior
Category configuration:
Proficiency level: Entry
Category configuration:
Proficiency level: Regular
Category configuration:
Proficiency level: Senior
Category configuration:
Proficiency level: Entry
Category configuration:
Proficiency level: Regular
Category configuration:
Proficiency level: Senior
Category configuration:
Proficiency level: Entry
Category configuration:
Proficiency level: Entry
Category configuration:
Proficiency level: Senior
Category configuration:
Proficiency level: Entry
Category configuration:
Proficiency level: Regular
Category configuration:
Proficiency level: Senior
Category configuration:
Proficiency level: Entry
Category configuration:
Proficiency level: Regular
Category configuration:
Proficiency level: Senior
Category configuration:
Proficiency level: Entry
Category configuration:
Proficiency level: Regular
Category configuration:
Proficiency level: Senior
Category configuration:
Proficiency level: Entry
Category configuration:
Proficiency level: Regular
Category configuration:
Proficiency level: Senior
Category configuration:
Proficiency level: Entry
Category configuration:
Proficiency level: Regular
Category configuration:
Proficiency level: Senior
Category configuration:
Proficiency level: Entry
Category configuration:
Proficiency level: Regular
Category configuration:
Proficiency level: Senior
Category configuration:
Proficiency level: Entry
Category configuration:
Proficiency level: Regular
Category configuration:
Proficiency level: Senior
Category configuration:
Proficiency level: Entry
Category configuration:
Proficiency level: Regular
Category configuration:
Proficiency level: Senior
Category configuration:
Proficiency level: Entry
Category configuration:
Proficiency level: Regular
Category configuration:
Proficiency level: Senior
Category configuration:
Proficiency level: Entry
Category configuration:
Proficiency level: Regular
Category configuration:
Proficiency level: Senior
Category configuration:
Proficiency level: Entry
Category configuration:
Proficiency level: Regular
Category configuration:
Proficiency level: Senior
Category configuration:
Proficiency level: Entry
Category configuration:
Proficiency level: Regular
Category configuration:
Proficiency level: Senior
Category configuration:
Proficiency level: Regular
Category configuration:
Proficiency level: Entry
Category configuration:
Proficiency level: Regular
Category configuration:
Proficiency level: Senior
Category configuration:
Proficiency level: Entry
Category configuration:
Proficiency level: Regular
Category configuration:
Proficiency level: Senior
Category configuration:
Proficiency level: Entry
Category configuration:
Proficiency level: Regular
Category configuration:
Proficiency level: Senior
Category configuration:
Proficiency level: Entry
Category configuration:
Proficiency level: Regular
Category configuration:
Proficiency level: Senior
Category configuration:
Proficiency level: Entry
Category configuration:
Proficiency level: Regular
Category configuration:
Proficiency level: Senior
Category configuration:
Proficiency level: Entry
Category configuration:
Proficiency level: Regular
Category configuration:
Proficiency level: Senior
Category configuration:
Proficiency level: Entry
Category configuration:
Proficiency level: Regular
Category configuration:
Proficiency level: Senior
Category configuration:
Proficiency level: Entry
Category configuration:
Proficiency level: Entry
Category configuration:
Proficiency level: Regular
Category configuration:
Proficiency level: Senior
Category configuration:
Proficiency level: Entry
Category configuration:
Proficiency level: Regular
Category configuration:
Proficiency level: Senior
Category configuration:
Proficiency level: Entry
Category configuration:
Proficiency level: Regular
Category configuration:
Proficiency level: Senior
Category configuration:
Proficiency level: Entry
Category configuration:
Proficiency level: Regular
Category configuration:
Proficiency level: Senior
Category configuration:
Proficiency level: Entry
Category configuration:
Proficiency level: Regular
Category configuration:
Proficiency level: Senior
Category configuration:
Proficiency level: Entry
Category configuration:
Proficiency level: Regular
Category configuration:
Proficiency level: Senior
Category configuration:
Proficiency level: Entry
Category configuration:
Proficiency level: Regular
Category configuration:
Proficiency level: Senior
Category configuration:
Proficiency level: Entry
Category configuration:
Proficiency level: Regular
Category configuration:
Proficiency level: Senior
Category configuration:
Proficiency level: Entry
Category configuration:
Proficiency level: Regular
Category configuration:
Proficiency level: Senior
Category configuration:
Proficiency level: Entry
Category configuration:
Proficiency level: Regular
Category configuration:
Proficiency level: Senior
Category configuration:
Proficiency level: Entry
Category configuration:
Proficiency level: Regular
Category configuration:
Proficiency level: Senior
Category configuration:
Proficiency level: Entry
Category configuration:
Proficiency level: Regular
Category configuration:
Proficiency level: Senior
Category configuration:
Proficiency level: Entry
Category configuration:
Proficiency level: Regular
Category configuration:
Proficiency level: Senior
Category configuration:
Covered topics
3D graphics and rendering fundamentals 
3D graphics and rendering fundamentals involve creating and displaying three-dimensional objects, scenes, and animations using mathematical models and algorithms. They cover concepts such as modeling, lighting, shading, textures, and rendering pipelines to produce realistic visuals.
5G Networks 
5G networks are the fifth generation of wireless technology, offering faster speeds, lower latency, and higher capacity compared to previous generations. They enable advanced applications like IoT, smart cities, and real-time connectivity for devices and services.
AI model security and governance 
AI model security and governance involve protecting AI systems from misuse, attacks, and data leakage while ensuring ethical and compliant use. It includes policies, controls, and monitoring to manage risks, maintain transparency, and meet regulatory requirements throughout the model lifecycle.
API mocking and virtualization 
API mocking and virtualization involve creating simulated API responses to test applications without relying on a live backend. This helps developers and testers work in parallel, improving efficiency and ensuring reliable testing in various scenarios.
API testing tools (Postman, SoapUI) 
API testing tools like Postman and SoapUI are used to validate the functionality, performance, and security of APIs by sending requests and analyzing responses. These tools help developers and testers automate testing, detect bugs, and ensure seamless API communication.
ASP.NET Core 
ASP.NET Core is a cross-platform, high-performance framework for building modern, cloud-based, and web applications with .NET.
AWS administration 
AWS administration involves managing and maintaining Amazon Web Services (AWS) cloud infrastructure, including tasks such as provisioning resources, configuring services, monitoring performance, and ensuring security and compliance.
AWS security 
AWS security refers to the comprehensive measures, protocols, and tools implemented to safeguard data, applications, and infrastructure within Amazon Web Services (AWS) cloud environment. It encompasses various layers of protection, including identity management, encryption, network security, and continuous monitoring, ensuring robust defense against potential threats and unauthorized access.
Accessibility standards and compliance (WCAG) 
Accessibility standards and compliance, such as WCAG (Web Content Accessibility Guidelines), ensure that digital products are usable by people with disabilities. These guidelines focus on making web and app content perceivable, operable, understandable, and robust for inclusive user experiences.
Active Directory administration 
Active Directory administration involves managing and maintaining Microsoft's Active Directory services, including user accounts, groups, permissions, and network resources to ensure secure and efficient access control within an organization.
Active Directory security 
Active Directory is a directory service developed by Microsoft for Windows domain networks. Windows Server operating systems include it as a set of processes and services.
Active Record ORM 
Active Record ORM is a Ruby on Rails feature that maps database tables to Ruby objects, enabling developers to interact with the database using object-oriented methods.
Adversarial machine learning 
Adversarial machine learning studies techniques for attacking and defending machine learning models using malicious or manipulated inputs. It focuses on improving model robustness against threats such as evasion attacks, data poisoning, and model exploitation.
Adversary emulation 
Adversary emulation is a cybersecurity assessment method that aims to test an organization's security controls against the tactics, techniques, and procedures (TTPs) used by threat actors posing the greatest risk to its industry.
Agile project management 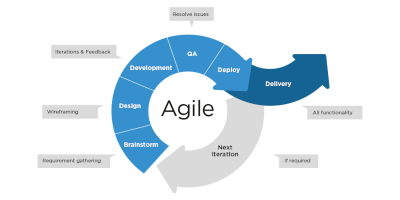
Agile project management is an iterative approach that focuses on flexibility, collaboration, and continuous improvement to deliver projects efficiently. It emphasizes adaptive planning, rapid feedback, and incremental progress through frameworks like Scrum and Kanban.
Android OS security 
Android is a mobile operating system based on a modified version of the Linux kernel and other open-source software, designed primarily for touchscreen mobile devices such as smartphones and tablets. Android is developed by a consortium of developers known as the Open Handset Alliance, though its most widely used version is primarily developed by Google.
Android application development 
Android application development is the process of creating software applications for devices running the Android operating system. It involves using tools like Android Studio and programming languages such as Java or Kotlin to design, build, and deploy mobile apps.
Android application security 
Android is a mobile operating system based on a modified version of the Linux kernel and other open-source software, designed primarily for touchscreen mobile devices such as smartphones and tablets. Android is developed by a consortium of developers known as the Open Handset Alliance, though its most widely used version is primarily developed by Google.
Angular Framework 
Angular Framework is a TypeScript-based framework for building dynamic, single-page web applications with a robust architecture and powerful tools.
Apache Spark (core, streaming, SQL) 
Apache Spark is a fast, distributed computing framework for big data processing, offering components like Spark Core for general execution, Spark Streaming for real-time data processing, and Spark SQL for structured data queries. It enables scalable, in-memory computing to accelerate data analytics and machine learning tasks.
Axum Framework 
Axum is a web framework for the Rust programming language that focuses on ergonomics, performance, and safety. It leverages Rust's strong type system and async capabilities to build scalable and secure web applications with minimal boilerplate.
Azure administration 
Azure administration involves managing and maintaining Microsoft Azure cloud services, including tasks such as provisioning resources, configuring services, monitoring performance, and ensuring security and compliance within the Azure environment.
Azure security 
Azure Security refers to security tools and capabilities available on Microsoft’s Azure cloud platform.
Backup and recovery solutions 
Backup and recovery solutions involve creating copies of data and systems to protect against loss, corruption, or disasters. They enable rapid restoration of operations, ensuring business continuity and data integrity.
Bash - code challenges 
Understanding the source code, the ability to make modifications and create new code is an important skill in many IT areas. This opens up the possibility of working more effectively and solving a very wide range of problems.
Big Data Analytics 
Big Data Analytics is the process of examining large and complex datasets to uncover patterns, trends, and insights for informed decision-making. It utilizes advanced techniques like machine learning, statistical analysis, and data mining to extract meaningful information.
Blockchain architecture and protocols 
Blockchain architecture and protocols define how distributed ledgers operate, including how data is stored, validated, and shared across decentralized networks. They establish rules for consensus, security, and communication between nodes to ensure trustless and tamper-resistant transactions.
Blueprint visual scripting 
Blueprint visual scripting is a node-based programming system that allows developers to create game logic without writing code. It enables rapid prototyping and gameplay development by visually connecting logic, events, and behaviors.
Budget and resource management 
Budget and resource management involve planning, allocating, and controlling financial and material resources to ensure a project's success. Effective management optimizes costs, prevents overspending, and ensures the efficient use of personnel, time, and materials.
C# - code challenges 
Understanding the source code, the ability to make modifications and create new code is an important skill in many IT areas. This opens up the possibility of working more effectively and solving a very wide range of problems.
C# programming language 
C# is a modern, object-oriented programming language developed by Microsoft for building a wide range of applications, including web, desktop, and mobile. It is known for its versatility, strong typing, and integration with the .NET framework for enhanced productivity and scalability.
C++ - code challenges 
C++ is a high-performance programming language that supports multiple paradigms, including object-oriented, procedural, and generic programming. It is widely used for developing applications requiring efficiency, such as games, operating systems, and embedded systems.
C++ programming language 
C++ is a high-performance programming language that supports multiple paradigms, including object-oriented, procedural, and generic programming. It is widely used for developing applications requiring efficiency, such as games, operating systems, and embedded systems.
CI/CD 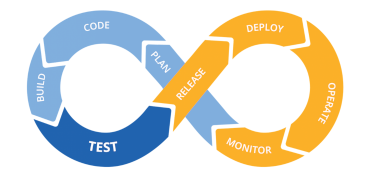
Continuous Integration and Continuous Delivery (CI/CD) is a software development practice that automates the process of integrating code changes, running tests, and deploying updates to ensure rapid, reliable, and consistent delivery of applications.
COMSEC system engineering 
COMSEC is used to protect both classified and unclassified traffic on military communications networks, including voice, video, and data. It is used for both analog and digital applications, and both wired and wireless links.
CSS3 
CSS3 is the latest version of Cascading Style Sheets, used to define the look and layout of web pages with advanced styling features and effects.
Check Point configuration and administration 
Check Point configuration and administration involve setting up and managing Check Point Software's cybersecurity appliances, including firewalls and security gateways, to secure network traffic, enforce policies, and protect against threats.
Cisco configuration and administration 
Cisco network devices are hardware solutions, such as routers, switches, and firewalls, designed to enable and optimize data communication within networks. They provide reliable connectivity, advanced security, and scalable networking solutions for businesses and enterprises.
Cloud 
Cloud computing is the delivery of computing services—including servers, storage, databases, networking, software, analytics, and intelligence—over the internet (“the cloud”) to offer faster innovation, flexible resources, and economies of scale.
Cloud Forensics 
Cloud Forensics involves examining and analyzing data and activities in cloud environments to investigate and address security incidents or legal issues.
Computer networks 
Computer Networking is the practice of connecting computers together to enable communication and data exchange between them.
Conflict resolution and team dynamics 
Conflict resolution and team dynamics involve managing disagreements and fostering collaboration to maintain a productive work environment. Effective strategies, such as active listening, mediation, and clear communication, help teams build trust and work efficiently toward common goals.
Containerization technologies 
Containerization technologies package applications and their dependencies into isolated, lightweight containers, ensuring consistent performance across different environments and simplifying deployment and scaling.
Continuous improvement techniques (Kaizen, retrospectives) 
Continuous improvement techniques, such as Kaizen and retrospectives, focus on regularly evaluating and enhancing processes, products, or workflows. Kaizen promotes small, incremental changes, while retrospectives in Agile encourage teams to reflect on past work and implement improvements in future iterations.
Contract testing (Pact, Spring Cloud Contract) 
Contract testing, using tools like Pact and Spring Cloud Contract, ensures that services in a microservices architecture communicate correctly by verifying API agreements between consumers and providers. It helps prevent integration issues by testing expected request-response interactions in isolation.
Cryptography 
Cryptography is the process of hiding or coding information so that only the person a message was intended for can read it. The art of cryptography has been used to code messages for thousands of years and continues to be used in bank cards, computer passwords, and ecommerce.
Data Engineering 
Data engineering focuses on designing, building, and maintaining systems that collect, store, and process large volumes of data efficiently. It involves developing data pipelines, optimizing databases, and ensuring data quality for analytics and machine learning applications.
Data Governance 
Data governance is the framework of policies, processes, and standards that ensure the effective management, quality, and security of an organization's data. It helps maintain data integrity, compliance, and accessibility for better decision-making and regulatory adherence.
Data Science 
Data Science is an interdisciplinary field that uses statistical methods, machine learning, and data analysis to extract insights and knowledge from structured and unstructured data. It combines programming, mathematics, and domain expertise to solve complex problems and drive data-driven decisions.
Data Visualization (Tableau, Power BI, matplotlib) 
Data visualization involves transforming raw data into graphical representations to identify patterns, trends, and insights effectively. Tools like Tableau, Power BI, and Matplotlib help create interactive dashboards and charts for better data-driven decision-making.
Data lake design and optimization 
Data lake design and optimization involve structuring large-scale storage systems to efficiently store, manage, and process raw and structured data. Optimization techniques include schema enforcement, indexing, and data partitioning to enhance performance, accessibility, and cost-efficiency.
Data protection and replication 
Data protection and replication involve safeguarding data against loss by creating copies and synchronizing them across multiple locations. These practices ensure high availability, fault tolerance, and rapid recovery in case of failures.
Database Design and Normalization 
Database Design involves structuring a database to efficiently store and manage data according to user needs and performance goals, while Normalization is the process of organizing this data to reduce redundancy and dependency by dividing it into related tables and defining the relationships between them.
Decentralized application (DApp) development 
Decentralized application (DApp) development involves creating applications that run on blockchain networks instead of centralized servers. These apps use smart contracts to ensure transparency, security, and user control without relying on a single authority.
Deep learning frameworks (TensorFlow, PyTorch) 
Deep learning frameworks like TensorFlow and PyTorch provide tools and libraries for building, training, and deploying neural networks efficiently. They enable researchers and developers to create advanced AI models for tasks such as image recognition, natural language processing, and autonomous systems.
Demo lab 
A collection of practical lab tasks to demonstrate live labs feature.
DevOps 
DevOps is a collaborative approach that combines development and IT operations to improve efficiency, accelerate software delivery, and enhance the quality of applications through automation and continuous integration/continuous delivery (CI/CD) practices.
Diesel ORM for Rust 
Diesel is a type-safe, high-performance ORM for Rust that allows developers to interact with databases using Rust’s strong type system. It provides compile-time query validation, ensuring safety and efficiency while reducing runtime errors in database operations.
Digital forensics 
Digital forensics refers to the process of collecting, preserving, analyzing, and presenting digital evidence from computer systems, networks, and digital devices to investigate cybercrimes, security incidents, and data breaches. Digital forensics enables cybersecurity professionals and law enforcement agencies to uncover the root causes of security incidents, identify perpetrators, and gather evidence for legal proceedings and incident response activities.
Digital forensics lab 
A collection of practical lab tasks on Digital forensics. Digital forensics refers to the process of collecting, preserving, analyzing, and presenting digital evidence from computer systems, networks, and digital devices to investigate cybercrimes, security incidents, and data breaches. Digital forensics enables cybersecurity professionals and law enforcement agencies to uncover the root causes of security incidents, identify perpetrators, and gather evidence for legal proceedings and incident response activities.
Disaster recovery planning and testing 
Disaster recovery planning and testing involve preparing strategies to restore systems and data after major disruptions or failures. Regular testing ensures recovery procedures are effective, minimizing downtime and data loss.
Distributed data processing architectures 
Distributed data processing architectures divide large datasets across multiple computing nodes to process data in parallel, improving performance and scalability. They are commonly used in big data frameworks like Hadoop and Apache Spark to handle complex computations efficiently.
Django Framework 
Django is a high-level Python framework for building web applications quickly, with a focus on simplicity, scalability, and built-in features for security and database management.
Django ORM 
Django ORM (Object-Relational Mapping) is a feature of the Django framework that allows developers to interact with a database using Python objects instead of raw SQL queries.
Docker containers 
Docker containers are lightweight, standalone, and portable software packages that encapsulate applications and their dependencies, allowing them to run reliably and consistently across different computing environments. They enable efficient deployment, scaling, and isolation of applications, promoting flexibility and ease of development.
Drogon Framework 
Drogon is a high-performance, asynchronous web framework for C++ designed for building fast and scalable web applications and APIs. It supports modern C++ features, routing, middleware, and database integration, making it efficient for real-time and high-concurrency applications.
ETL Development 
ETL (Extract, Transform, Load) development involves designing processes to extract data from various sources, transform it into a usable format, and load it into a target system, such as a data warehouse. It ensures data consistency, quality, and readiness for analysis and reporting.
Edge computing architecture and orchestration 
Edge computing architecture and orchestration involve designing and managing distributed computing resources located close to data sources. This approach reduces latency and bandwidth usage by processing data locally while coordinating workloads across edge and central systems.
Eloquent ORM 
Eloquent ORM is Laravel's built-in Object-Relational Mapping tool that simplifies database interactions by allowing developers to use PHP objects for querying and managing data.
Embedded systems programming 
Embedded systems programming involves developing software for specialized computing devices that operate within larger systems, such as IoT devices, automotive controls, and medical equipment. It requires optimizing code for performance, reliability, and resource constraints using languages like C and C++.
Entity Framework Core 
Entity Framework Core is a cross-platform ORM for .NET that simplifies database access by mapping .NET objects to database tables and providing an abstraction for data operations.
Feature engineering and data preprocessing 
Feature engineering and data preprocessing involve transforming raw data into a suitable format for machine learning models by selecting, creating, and optimizing relevant features. These steps improve model accuracy and performance through techniques like normalization, handling missing values, and encoding categorical data.
File System Analysis 
File System Analysis in Digital Forensics involves examining file structures and metadata to recover, identify, and interpret digital evidence related to data storage and manipulation.
GCP administration 
Google Cloud Platform administration involves managing and maintaining GCP resources, configuring services, monitoring performance, and ensuring security and compliance within Google's cloud infrastructure.
GCP security 
Google Cloud Platform security administration involves managing and implementing security measures to protect GCP resources, including configuring access controls, monitoring for threats, and ensuring compliance with security policies.
GORM ORM for Go 
GORM is a powerful and flexible ORM for Go that simplifies database interactions by providing an intuitive, developer-friendly API. It supports features like automatic migrations, associations, transactions, and query building while maintaining performance and scalability.
Game optimization and performance profiling 
Game optimization and performance profiling involve analyzing and improving a game’s performance to ensure smooth gameplay across devices. These processes identify bottlenecks in rendering, physics, and logic to reduce lag, memory usage, and frame drops.
Game physics and animation systems 
Game physics and animation systems handle the simulation of movement, collisions, and physical interactions in games. They work together to create realistic motion, character behavior, and immersive visual experiences.
Gin Framework 
Gin is a lightweight and high-performance web framework for Golang, designed for building fast and scalable web applications and APIs. It features a minimalistic design with middleware support, routing, and JSON validation, making it ideal for efficient request handling.
Git 
Git is a distributed version control system that tracks changes in source code during software development, enabling multiple developers to collaborate efficiently and manage project history.
Go - code challenges 
Go, or Golang, is a statically typed, compiled programming language designed by Google for simplicity, performance, and scalability. It is ideal for building modern distributed systems, offering features like concurrency and garbage collection.
Go programming language 
Go, or Golang, is a statically typed, compiled programming language designed by Google for simplicity, performance, and scalability. It is ideal for building modern distributed systems, offering features like concurrency and garbage collection.
GraphQL API testing 
GraphQL API testing involves validating queries, mutations, and responses to ensure correct functionality, performance, and security. It focuses on testing schema structure, data retrieval, and error handling to optimize API efficiency and reliability.
HTML5 
HTML5 is the latest version of the Hypertext Markup Language used for structuring and presenting content on the web, offering new elements and features for richer web applications.
HTTP Protocol 
The HTTP protocol is a communication protocol used for transmitting data over the web, allowing web browsers and servers to exchange information.
Hadoop ecosystem (HDFS, MapReduce, Hive) 
The Hadoop ecosystem is a collection of open-source tools for processing and managing big data, with HDFS for distributed storage, MapReduce for parallel data processing, and Hive for SQL-based querying. These components work together to enable scalable and efficient handling of large datasets.
Hibernate ORM 
Hibernate ORM is a Java framework that simplifies database interactions by mapping Java objects to database tables and handling data persistence with object-oriented methods.
ISTQB Certified Tester 
ISTQB Certified Tester is a professional qualification for software testers, validating their knowledge and skills in software testing principles, techniques, and best practices.
ITIL Service Operation 
ITIL Service Operation focuses on delivering and managing IT services to ensure they run smoothly and efficiently, including incident management, problem management, and operational control.
IaaC 
Infrastructure as Code (IaaC) is the practice of managing and provisioning computing infrastructure through machine-readable configuration files, enabling automated and consistent deployment of resources.
Incident handling 
Incident handling in cybersecurity is the process of identifying, managing, and responding to security breaches or threats to minimize damage and restore normal operations.
Incident response 
Incident response refers to the structured process of identifying, managing, and mitigating security incidents and breaches within an organization's IT infrastructure. It involves a coordinated effort by security teams to detect, analyze, contain, eradicate, and recover from cybersecurity incidents in order to minimize the impact on the organization's operations, assets, and reputation.
Industrial Control Systems (ICS) and SCADA 
Industrial Control Systems (ICS) are integrated hardware and software solutions used to monitor and control industrial processes in sectors like manufacturing, energy, and water treatment. SCADA (Supervisory Control and Data Acquisition) is a subset of ICS that enables real-time data collection, remote control, and automation of critical infrastructure.
Industrial Control Systems (ICS) and SCADA security 
Industrial Control Systems (ICS) and SCADA security focus on protecting critical infrastructure from cyber threats, unauthorized access, and operational disruptions. It involves implementing measures like network segmentation, encryption, and intrusion detection to ensure the reliability and safety of industrial processes.
Industrial network protocols (MODBUS, DNP3, PROFINET) 
Industrial network protocols like MODBUS, DNP3, and PROFINET enable communication between devices in industrial automation and control systems. They facilitate data exchange, remote monitoring, and real-time control in sectors such as manufacturing, energy, and utilities.
Interaction design principles 
Interaction design principles focus on creating intuitive, efficient, and enjoyable user interactions with digital products. Key principles include consistency, feedback, simplicity, and usability to enhance user engagement and experience.
Java - code challenges 
Understanding the source code, the ability to make modifications and create new code is an important skill in many IT areas. This opens up the possibility of working more effectively and solving a very wide range of problems.
Java programming language 
Java is a versatile, object-oriented programming language designed for cross-platform compatibility, allowing code to run on any device with a Java Virtual Machine (JVM). It is widely used for building web, mobile, and enterprise applications due to its reliability and scalability.
JavaScript - code challenges 
Understanding the source code, the ability to make modifications and create new code is an important skill in many IT areas. This opens up the possibility of working more effectively and solving a very wide range of problems.
Juniper configuration and administration 
Juniper configuration and administration involve setting up and managing Juniper Networks' networking and security devices, including routers, switches, and firewalls, to ensure efficient and secure network operations.
Kafka and real-time data streaming 
Kafka is a distributed event streaming platform designed for high-throughput, real-time data processing and messaging. It enables scalable, fault-tolerant data streaming between applications, making it ideal for event-driven architectures and big data analytics.
Kanban methodologies 
Kanban methodologies focus on visualizing workflow, limiting work in progress, and optimizing efficiency in project management. Using a Kanban board, teams track tasks through stages, enabling continuous delivery and adaptive process improvements.
Kubernetes administration 
Kubernetes administration involves managing, configuring, and maintaining Kubernetes clusters to ensure reliable container orchestration. It includes tasks such as deployment, scaling, monitoring, and troubleshooting to keep applications running efficiently.
Kubernetes security 
Kubernetes security involves protecting cluster resources, workloads, and configurations from unauthorized access and vulnerabilities. It includes implementing measures such as role-based access control (RBAC), network policies, secrets management, and continuous monitoring to ensure a secure containerized environment.
Laravel Framework 
Laravel is a PHP framework for web development that provides an elegant syntax, powerful tools, and a robust ecosystem for building modern, scalable applications.
Linux administration 
Linux is an open source operating system (OS). An operating system is the software that directly manages a system's hardware and resources, like CPU, memory, and storage. Linux is most popular Operating System for servers and smartphones (as Android OS is build upon Linux).
Linux administration lab 
A collection of practical lab tasks on Linux administration. Linux is an open source operating system (OS). An operating system is the software that directly manages a system's hardware and resources, like CPU, memory, and storage. Linux is most popular Operating System for servers and smartphones (as Android OS is build upon Linux).
Linux malware analysis lab 
A collection of practical lab tasks on Linux malware analysis. Linux malware analysis is the process of examining malicious software (malware) designed to target Linux systems. This involves identifying, dissecting, and understanding the malware's behavior, functionality, and impact. The analysis helps in detecting infections, determining how the malware operates, and developing strategies for mitigation, prevention, and remediation on Linux-based environments.
Linux security 
Linux is an open source operating system (OS). An operating system is the software that directly manages a system's hardware and resources, like CPU, memory, and storage. Linux is most popular Operating System for servers and smartphones (as Android OS is build upon Linux).
Linux security lab 
A collection of practical lab tasks on Linux security. Linux is an open source operating system (OS). An operating system is the software that directly manages a system's hardware and resources, like CPU, memory, and storage. Linux is most popular Operating System for servers and smartphones (as Android OS is build upon Linux).
Load testing for APIs 
Load testing for APIs evaluates an API’s performance under different levels of traffic to ensure stability and scalability. It helps identify bottlenecks, response times, and system limits by simulating real-world usage conditions.
MLOps 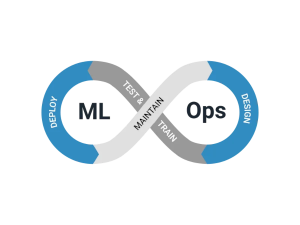
MLOps (Machine Learning Operations) is a set of practices that streamline the deployment, monitoring, and management of machine learning models in production. It combines DevOps, data engineering, and machine learning to ensure model reliability, scalability, and continuous improvement.
MS SQL Database administration 
MS SQL Database Administration involves managing and maintaining Microsoft SQL Server databases, including tasks such as installation, configuration, performance tuning, and security management to ensure optimal operation and data integrity.
MS SQL Database backup and recovery 
MS SQL Database Backup and Recovery is the process of creating copies of database data to protect against loss and restoring that data from backups in case of failure or corruption.
MS SQL Database high availability and clustering 
MS SQL Database High Availability and Clustering involve configuring systems to ensure continuous database access and minimize downtime by using redundant servers and failover mechanisms.
MS SQL Database performance tuning and monitoring 
MS SQL Database Performance Tuning and Monitoring involves adjusting and optimizing database settings and queries to enhance performance and continuously tracking system metrics to ensure efficient operation and identify potential issues.
MS SQL Database security and user management 
MS SQL Database Security and User Management involves implementing measures to protect database data from unauthorized access and managing user roles and permissions to control access and maintain security.
Machine Learning Algorithms 
Machine learning algorithms are computational methods that enable systems to learn patterns from data and make predictions or decisions without explicit programming. They include supervised, unsupervised, and reinforcement learning techniques for tasks like classification, clustering, and recommendation.
Malware dynamic analysis in Linux OS 
Malware dynamic analysis in Linux OS involves executing malicious software in a controlled environment to observe its behavior, analyze its actions in real-time, and identify potential security risks or threats specific to Linux-based systems.
Malware dynamic analysis in Windows OS 
Malware dynamic analysis in Windows OS involves executing malicious software in a controlled environment to observe its behavior, analyze its actions, and identify potential threats or vulnerabilities.
Malware static analysis in Linux OS 
Malware static analysis in Linux OS involves examining the code and structure of malicious software without executing it, aiming to understand its behavior, identify patterns, and develop detection and mitigation strategies specific to Linux environments.
Malware static analysis in Windows OS 
Malware static analysis in Windows OS involves examining the code and structure of malicious software without executing it, aiming to understand its behavior, identify indicators of compromise (IOCs), and develop detection and prevention strategies.
Memory Forensics 
Memory Forensics involves analyzing a computer's volatile memory (RAM) to uncover evidence of malicious activity, running processes, and system states.
Microservices Architecture 
Microservices Architecture is a design approach where applications are composed of small, independent services that communicate over networks, allowing for flexible and scalable development.
Mobile Device Forensics 
Mobile Device Forensics is the process of retrieving and analyzing data from mobile devices to investigate and gather evidence for legal or security purposes.
Modern JavaScript 
Modern JavaScript refers to the latest standards and features of JavaScript, including ES6 and beyond, which enhance the language with new syntax, functions, and capabilities.
Modern software development fundamentals 
Modern software development fundamentals encompass agile methodologies, continuous integration/continuous delivery (CI/CD), version control, automated testing, and collaborative tools to enhance efficiency, quality, and responsiveness in software creation.
Modern software testing fundamentals 
Modern software testing fundamentals encompass agile testing methodologies, test automation, continuous integration and continuous delivery (CI/CD), exploratory testing, and integration of testing into the software development lifecycle (SDLC) to ensure software quality and efficiency.
Monitoring and observability 
Monitoring and observability involve tracking system performance, health, and behavior using metrics, logs, and traces. They help teams detect issues, understand system state, and maintain reliability in complex distributed environments.
MySQL Database administration 
MySQL Database Administration involves managing and maintaining MySQL databases, including tasks such as installation, configuration, performance tuning, and security to ensure optimal operation and data integrity.
MySQL Database backup and recovery 
MySQL Database Backup and Recovery involves creating and managing backups of MySQL data to protect against loss and restoring that data from backups in case of failure or corruption.
MySQL Database high availability and clustering 
MySQL Database High Availability and Clustering involves setting up redundant servers and failover mechanisms to ensure continuous database access and minimize downtime.
MySQL Database performance tuning and monitoring 
MySQL Database Performance Tuning and Monitoring involves optimizing database queries and configurations to enhance performance and tracking system metrics to ensure efficient operation and detect issues.
MySQL Database security and user management 
MySQL Database Security and User Management involves safeguarding database access through authentication and authorization, and managing user roles and permissions to ensure data protection and control.
NAS technologies 
NAS (Network Attached Storage) technologies provide file-level data storage over a network for easy access and sharing. They offer centralized, scalable, and cost-effective storage solutions for organizations and home users.
NATO security policies and procedures 
Security policies and procedures are formal guidelines and instructions designed to protect an organization's information, assets, and operations from threats and vulnerabilities.
Natural Language Processing (NLP) 
Natural Language Processing (NLP) is a branch of artificial intelligence that enables computers to understand, interpret, and generate human language. It powers applications like chatbots, sentiment analysis, and machine translation by leveraging linguistic algorithms and machine learning.
Network Forensics 
Network Forensics involves monitoring and analyzing network traffic to detect, investigate, and respond to security incidents and unauthorized activities.
Network security 
Network security is a critical aspect of modern cybersecurity, and covers a wide range of topics, including firewall configurations, intrusion detection and prevention, secure network design, VPN implementation, access controls, and more.
Network security logs analysis .png)
Network security logs analysis in the context of cybersecurity involves the examination and interpretation of logs generated by various network devices and systems to identify potential security threats, anomalies, and malicious activities. Network security logs provide valuable insights into the behavior of network traffic, user activities, and system events, helping organizations detect and respond to cybersecurity incidents effectively.
Network traffic capture analysis 
Network traffic capture analysis, also known as packet analysis, is a process used in cybersecurity to examine and interpret the data packets transmitted over a network. It involves capturing network traffic in real-time or from stored packet capture files and analyzing the contents of the packets to gain insights into network behavior and identify security threats.
ODB ORM for C++ 
ODB is an object-relational mapping (ORM) framework for C++ that enables seamless database integration by mapping C++ objects to relational database tables. It automates query generation, schema evolution, and transaction management while maintaining high performance and type safety.
Operating Systems Forensics 
Operating Systems Forensics involves analyzing and investigating operating systems to uncover and evaluate evidence related to security incidents, system breaches, or unauthorized activities.
Oracle Database administration 
Oracle Database Administration involves managing and maintaining Oracle databases, including installation, configuration, performance tuning, and security to ensure optimal operation and data integrity.
Oracle Database backup and recovery 
Oracle Database Backup and Recovery involves creating backups of Oracle data to prevent loss and restoring that data from backups in case of failure or corruption.
Oracle Database high availability and clustering 
Oracle Database High Availability and Clustering involves setting up redundant systems and failover mechanisms to ensure continuous database access and minimize downtime.
Oracle Database performance tuning and monitoring 
Oracle Database Performance Tuning and Monitoring involves optimizing queries and system settings to enhance performance and tracking metrics to ensure efficient operation and identify issues.
Oracle Database security and user management 
Oracle Database Security and User Management involves safeguarding data through access controls and managing user roles and permissions to ensure secure and authorized access.
PHP - code challenges 
Understanding the source code, the ability to make modifications and create new code is an important skill in many IT areas. This opens up the possibility of working more effectively and solving a very wide range of problems.
PHP8 programming language 
PHP 8 is a major version of the PHP scripting language used primarily for web development, offering improved performance and modern features. It introduces innovations like the Just-In-Time (JIT) compiler and union types for more efficient and flexible coding.
PLC programming and configuration 
PLC (Programmable Logic Controller) programming and configuration involve developing and setting up control logic for industrial automation systems. Using languages like ladder logic and structured text, PLCs execute real-time operations in manufacturing, robotics, and process control.
Palo Alto configuration and administration 
Palo Alto configuration and administration involve setting up and managing Palo Alto Networks' firewall and cybersecurity devices to ensure secure network operations, including policies, rules, and threat prevention configurations.
Pentesting lab 
A collection of practical lab tasks on Pentesting. Pentesting, or penetration testing, is the practice of simulating cyberattacks on a system, network, or application to identify vulnerabilities that could be exploited by attackers. The goal is to assess the security of the target by discovering weaknesses and providing insights for improving defenses before real threats can exploit them.
Performance tuning and capacity planning 
Performance tuning and capacity planning involve optimizing system performance while ensuring sufficient resources to handle current and future workloads. These practices help prevent bottlenecks, reduce downtime, and support scalable growth.
Play Framework 
Play Framework is a high-performance, reactive web framework for building scalable applications using the Scala and Java programming languages. It follows a lightweight, asynchronous, and MVC-based architecture, making it ideal for modern web and API development.
PostgreSQL Database administration 
PostgreSQL Database Administration involves managing and maintaining PostgreSQL databases, including tasks such as installation, configuration, performance tuning, and security to ensure optimal operation and data integrity.
PostgreSQL Database backup and recovery 
PostgreSQL Database Backup and Recovery involves creating backups of PostgreSQL data to protect against loss and restoring that data from backups in case of failure or corruption.
PostgreSQL Database high availability and clustering 
PostgreSQL Database High Availability and Clustering involves configuring redundant servers and failover systems to ensure continuous access and minimize downtime.
PostgreSQL Database performance tuning and monitoring 
PostgreSQL Database Performance Tuning and Monitoring involves optimizing queries and settings to enhance performance and tracking system metrics to ensure efficient operation and detect issues.
PostgreSQL Database security and user management 
PostgreSQL Database Security and User Management involves protecting data through authentication and authorization, and managing user roles and permissions to control access and ensure security.
PowerShell - code challenges 
Understanding the source code, the ability to make modifications and create new code is an important skill in many IT areas. This opens up the possibility of working more effectively and solving a very wide range of problems.
Product - Ansible 
Ansible is an open-source automation tool used for configuration management, application deployment, and task automation across multiple systems, simplifying IT operations.
Product - Splunk 
Splunk is a powerful software platform used for searching, monitoring, and analyzing machine-generated big data via a web-style interface. It collects and indexes data from various sources, allowing users to generate reports, visualize data, and gain real-time insights into their IT infrastructure, security systems, and business processes.
Product - Tenable Nessus 
Tenable Nessus is a widely used vulnerability scanning tool that helps identify and assess security issues within networks and systems, offering comprehensive insights and remediation guidance to enhance overall cybersecurity posture.
Project lifecycle management 
Project lifecycle management involves overseeing a project from initiation to completion, ensuring it meets objectives, timelines, and budget constraints. It includes key phases such as planning, execution, monitoring, and closure to ensure successful delivery and continuous improvement.
Prototyping tools (Figma, Sketch) 
Prototyping tools like Figma and Sketch allow UX/UI designers to create interactive and visual representations of digital products before development. These tools enable collaboration, user testing, and iterative design to refine the user experience efficiently.
Python - code challenges 
Understanding the source code, the ability to make modifications and create new code is an important skill in many IT areas. This opens up the possibility of working more effectively and solving a very wide range of problems.
Python3 programming language 
Python 3 is a versatile, high-level programming language known for its simplicity and readability, widely used in web development, data analysis, artificial intelligence, and more. It offers modern features, enhanced performance, and consistent syntax compared to earlier versions.
Quality assurance and control processes 
Quality assurance and control processes ensure that products or services meet defined standards through systematic testing and monitoring. While quality assurance focuses on preventing defects through process improvements, quality control involves identifying and correcting defects in the final output.
RESTful API Development 
RESTful API Development involves creating web services that use HTTP requests to access and manipulate resources in a stateless, scalable, and standardized manner.
React JS Framework 
React JS is a JavaScript library for building user interfaces with a component-based architecture and efficient rendering.
Real-time systems and automation 
Real-time systems and automation involve computing solutions that process and respond to inputs within strict time constraints to ensure precise and reliable operations. These systems are widely used in industries like manufacturing, robotics, and transportation to enable seamless automation and control.
Real-time systems development 
Real-time systems development focuses on designing software that processes data and responds to inputs within strict time constraints. These systems are used in applications like aerospace, automotive, and industrial automation, where timing and reliability are critical.
Red Teaming 
A red team plays the role of the attacker by trying to find vulnerabilities and break through cybersecurity defenses by using advanced techniques, tactics and procedures.
Reliability engineering principles 
Reliability engineering principles focus on designing systems that consistently perform as expected under defined conditions. They emphasize fault tolerance, redundancy, monitoring, and continuous improvement to minimize failures and downtime.
Requirements gathering and documentation 
Requirements gathering and documentation involve identifying, analyzing, and recording the needs and expectations of stakeholders for a project. Clear and structured documentation ensures alignment, reduces misunderstandings, and serves as a reference throughout the development process.
Responsive web design 
Responsive web design is an approach to creating web pages that adapt seamlessly to different screen sizes and devices for an optimal user experience.
Reverse engineering lab 
A collection of practical lab tasks on Reverse engineering. Reverse engineering is the process of analyzing a system, software, or device to understand its structure, functionality, and operation. By deconstructing the original product, reverse engineering aims to uncover how it was designed or how it works, often to replicate, modify, or enhance it, or to identify vulnerabilities. This technique is commonly used in software analysis, hardware design, and cybersecurity.
Risk assessments 
Risk assessments in cybersecurity are evaluations of potential threats and vulnerabilities to determine the likelihood and impact of security incidents on an organization's assets.
Risk management 
Risk management involves identifying, assessing, and mitigating potential threats and vulnerabilities to protect digital assets and information. It encompasses strategies and processes to analyze risks, prioritize them based on their potential impact, and implement measures to reduce or mitigate these risks, ensuring proactive protection and resilience against cybersecurity threats.
Ruby - code challenges 
Understanding the source code, the ability to make modifications and create new code is an important skill in many IT areas. This opens up the possibility of working more effectively and solving a very wide range of problems.
Ruby on Rails Framework 
Ruby on Rails is a web application framework written in Ruby that emphasizes convention over configuration, allowing for rapid development with a focus on simplicity and productivity.
Ruby3 programming language 
Ruby 3 is a dynamic, object-oriented programming language focused on simplicity and productivity, commonly used for web development. It introduces performance improvements, concurrency features like Ractor, and enhanced developer tools while maintaining its elegant and readable syntax.
Rust - code challenges 
Rust is a systems programming language focused on memory safety, performance, and concurrency. It prevents common bugs like null pointer dereferencing and data races without using a garbage collector.
Rust programming language 
Rust is a systems programming language focused on memory safety, performance, and concurrency. It prevents common bugs like null pointer dereferencing and data races without using a garbage collector.
SAN technologies 
SAN (Storage Area Network) technologies provide high-speed, dedicated networks that connect servers to shared storage resources. They enable scalable, reliable, and efficient block-level data access for enterprise storage environments.
SQL Indexing Strategies 
SQL Indexing Strategies involve creating and managing indexes on database tables to speed up data retrieval and improve query performance by reducing the amount of data scanned.
SQL Query Optimization 
SQL Query Optimization is the process of improving the performance and efficiency of a database query by refining its structure and execution plan to reduce response time and resource consumption.
Scala - code challenges 
Scala is a programming language that combines object-oriented and functional programming paradigms. It is designed for scalability, interoperability with Java, and concise, expressive code.
Scala programming language 
Scala is a programming language that combines object-oriented and functional programming paradigms. It is designed for scalability, interoperability with Java, and concise, expressive code.
Scrum framework (roles, artifacts, ceremonies) 
The Scrum framework is an Agile methodology that organizes work into sprints, with defined roles such as Scrum Master, Product Owner, and Development Team. It includes key artifacts like the Product Backlog, Sprint Backlog, and Increment, along with ceremonies such as Sprint Planning, Daily Standups, Sprint Review, and Sprint Retrospective to ensure continuous progress and improvement.
Secrets management and supply chain security 
Secrets management and supply chain security focus on protecting sensitive credentials and ensuring the integrity of software dependencies. They involve secure storage of secrets, access control, and preventing tampering or vulnerabilities in the software development and deployment pipeline.
Secure DevOps practices 
Secure DevOps practices integrate security into every stage of the software development and deployment lifecycle. They emphasize automation, continuous security testing, and collaboration between development, operations, and security teams to reduce risks and vulnerabilities.
Secure network design for OT environments 
Secure network design for OT (Operational Technology) environments involves implementing robust architectures to protect industrial control systems from cyber threats. It includes network segmentation, intrusion detection, and access control to ensure the safety, reliability, and resilience of critical infrastructure.
Secure web design and development 
Secure web design and development refers to the process of creating websites and web applications with security considerations integrated into every stage of the development lifecycle. It involves implementing best practices, adopting secure coding techniques, and leveraging security controls to protect against common web vulnerabilities and cyber threats.
Security Information and Event Management (SIEM) 
Security Information and Event Management (SIEM) products are software solutions designed to provide organizations with comprehensive visibility into their IT infrastructure's security posture. SIEM systems collect, analyze, and correlate security-related data from various sources across the organization, including network devices, servers, endpoints, applications, and security tools. The primary goal of SIEM is to help organizations detect and respond to security threats in real-time, as well as to facilitate compliance reporting and forensic analysis.
Security Operations Center (SOC) 
A Security Operations Center (SOC) is a centralized unit within an organization responsible for monitoring, detecting, analyzing, and responding to cybersecurity incidents and threats. It serves as a nerve center for cybersecurity activities, providing real-time monitoring, threat intelligence, incident analysis, and incident response capabilities.
Security architecture 
Security architecture in cybersecurity refers to the design, structure, and arrangement of security controls, protocols, and systems within an organization. It involves the planning and implementation of comprehensive strategies to protect digital assets, networks, and data from potential threats, ensuring a robust defense framework encompassing preventive, detective, and responsive measures against cyberattacks and vulnerabilities.
Security audit 
A security audit is a systematic assessment and examination of an organization's systems, networks, and policies to identify vulnerabilities, compliance gaps, and potential risks. It involves a thorough review of security controls, configurations, and practices to ensure they align with established security standards, regulations, and best practices, aiming to enhance overall security posture and mitigate potential threats.
Security awareness 
Security awareness is the knowledge and attitude members of an organization possess regarding the protection of the physical, and especially informational, assets of that organization.
Security governance 
Security governance in cybersecurity refers to the framework, policies, and processes implemented to guide and oversee an organization's security efforts. It involves defining responsibilities, establishing controls, and setting strategic directions to ensure that security measures align with business objectives, comply with regulations, and effectively mitigate risks across the entire organization.
Security logs analysis 
Security logs analysis in cybersecurity is the process of examining log data to detect, investigate, and respond to security incidents and threats.
Security, Orchestrations, Automation and Response (SOAR) 
Security, Orchestration, Automation, and Response (SOAR) is a cybersecurity term that refers to a set of technologies, processes, and practices designed to streamline and automate the management of security operations. SOAR platforms integrate security orchestration and automation capabilities with incident response workflows to improve the efficiency, consistency, and effectiveness of cybersecurity operations.
Slick ORM for Scala 
Slick is a functional relational mapping (FRM) library for Scala that enables type-safe, composable database interactions. It provides an expressive API for querying databases using Scala code, eliminating the need for raw SQL while maintaining performance and scalability.
Smart contracts development 
Smart contracts development involves creating self-executing programs that run on blockchain networks and automatically enforce agreements when conditions are met. It typically uses languages like Solidity or Rust to build secure, decentralized applications without intermediaries.
Smart contracts security 
Smart contracts security focuses on identifying and preventing vulnerabilities in blockchain-based smart contract code to avoid exploits and financial loss. It involves practices like code audits, formal verification, and secure development patterns to ensure contract reliability and integrity.
Spring Framework 
Spring Framework is a comprehensive Java framework that provides tools and libraries for building enterprise-level applications with features for dependency injection, aspect-oriented programming, and more.
Stakeholder management 
Stakeholder management involves identifying, engaging, and communicating with individuals or groups affected by a project to ensure their needs and expectations are met. Effective stakeholder management builds trust, reduces risks, and enhances project success through collaboration and transparency.
Statistics and probability for data analysis 
Statistics and probability for data analysis involve mathematical techniques to summarize, interpret, and make predictions from data. These concepts help identify patterns, measure uncertainty, and support decision-making in various analytical applications.
Storage systems administration 
Storage systems administration involves managing, configuring, and maintaining data storage infrastructure to ensure availability, performance, and security. It includes tasks such as capacity planning, backup integration, monitoring, and troubleshooting storage resources.
Swift - code challenges 
Swift is a powerful and intuitive programming language developed by Apple for building iOS, macOS, watchOS, and tvOS applications. It combines performance and safety with modern features, making it easy to write and maintain code.
Testing modern web applications 
Testing modern web applications involves evaluating their functionality, performance, security, and usability to ensure they meet specified requirements and perform well across different devices and browsers.
Threat hunting 
Threat hunting is a crucial aspect of modern cybersecurity, requiring a proactive and analytical mindset.
Token standards and DeFi protocols 
Token standards and DeFi protocols define rules for creating, managing, and exchanging digital assets on blockchain platforms. They enable interoperable tokens and decentralized financial services such as lending, trading, and staking without traditional intermediaries.
Tools for project management 
Project management tools, such as Jira, Trello, and Asana, help teams plan, track, and manage tasks efficiently. They provide features like task assignments, progress tracking, and collaboration to improve workflow and productivity.
TypeScript 
TypeScript is a superset of JavaScript that adds static typing and advanced features to improve code quality and development efficiency.
Unity engine fundamentals 
Unity engine fundamentals cover the core concepts and tools used to build games and interactive applications with the Unity engine. They include scene management, scripting, asset handling, physics, and rendering basics.
Unreal Engine fundamentals 
Unreal Engine fundamentals cover the core tools and concepts for creating high-quality games and real-time applications. They include level design, Blueprints, rendering, physics, and asset management.
Usability testing methodologies 
Usability testing methodologies involve evaluating a digital product by observing real users as they complete tasks to identify pain points and areas for improvement. Common methods include moderated testing, A/B testing, and remote usability tests to enhance user experience and functionality.
User experience research methods 
User experience research methods involve techniques like interviews, usability testing, surveys, and analytics to understand user behaviors, needs, and motivations. These methods help design intuitive and user-centered interfaces that enhance usability and satisfaction.
VMWare administration 
VMware is a leading virtualization technology company providing software that enables the creation, management, and deployment of virtual machines and cloud infrastructure, enhancing efficiency, scalability, and flexibility in IT environments.
Virtualization technologies 
Virtualization is technology that you can use to create virtual representations of servers, storage, networks, and other physical machines. Virtual software mimics the functions of physical hardware to run multiple virtual machines simultaneously on a single physical machine.
Vue.js Framework 
Vue.js is a progressive JavaScript framework for building user interfaces with a focus on simplicity and ease of integration.
Vulnerability assessment 
A vulnerability assessment is a systematic review and analysis process used to identify, quantify, and prioritize weaknesses within a system, network, or infrastructure to anticipate and mitigate potential security risks.
Web API security 
Web API security involves implementing measures to protect the integrity, confidentiality, and availability of data exchanged between web applications and APIs, safeguarding against unauthorized access, data breaches, and other security threats.
Web application development fundamentals 
Web application development fundamentals cover the basic principles and practices for designing, building, and deploying web applications, including client-server architecture, coding, and user interface design.
Web application pentesting lab 
A collection of practical lab tasks on Web application pentesting. Web application security is critical as these applications often serve as prime targets for cyberattacks. It covers a comprehensive range of topics, including secure coding practices, input validation, session management, SQL injection prevention, cross-site scripting (XSS) mitigation, and other common vulnerabilities.
Web application security 
Web application security is critical as these applications often serve as prime targets for cyberattacks. It covers a comprehensive range of topics, including secure coding practices, input validation, session management, SQL injection prevention, cross-site scripting (XSS) mitigation, and other common vulnerabilities.
Web application security - code challenges 
Understanding the source code, the ability to make modifications and create new code is an important skill in many IT areas. This opens up the possibility of working more effectively and solving a very wide range of problems.
Windows administration 
Windows is most popular Operating System for workstations in largest corporations and one of most popular Operating System for servers. It is crucial to understand its internals and be able to provide necessary configuration changes.
Windows administration lab 
A collection of practical lab tasks on Windows administration. Windows is most popular Operating System for workstations in largest corporations and one of most popular Operating System for servers. It is crucial to understand its internals and be able to provide necessary configuration changes.
Windows malware analysis lab 
A collection of practical lab tasks on Windows malware analysis. Windows malware analysis is the process of examining and understanding malicious software that targets Windows operating systems. This involves identifying, dissecting, and analyzing the malware to determine its behavior, functionality, and potential impact. The goal is to detect infections, understand how the malware operates, and develop strategies to mitigate, prevent, and remove it from Windows systems.
Windows security 
Windows is most popular Operating System for workstations in largest corporations and one of most popular Operating System for servers. It is crucial to understand its internals and be able to provide necessary configuration changes.
Windows security lab 
A collection of practical lab tasks on Windows security. Windows is most popular Operating System for workstations in largest corporations and one of most popular Operating System for servers. It is crucial to understand its internals and be able to provide necessary configuration changes.
iOS OS security 
iOS is a mobile operating system developed by Apple Inc. exclusively for its hardware. It is the operating system that powers many of the company's mobile devices, including the iPhone; the term also includes the system software for iPads (predating iPadOS, which was introduced in 2019) as well as on the iPod Touch devices. It is the world's second-most widely installed mobile operating system, after Android.
iOS application development 
iOS application development is the process of creating apps for Apple's iOS platform, which runs on iPhones, iPads, and other Apple devices. It uses tools like Xcode and programming languages such as Swift or Objective-C to design, build, and optimize apps for the Apple ecosystem.
iOS application security 
iOS is a mobile operating system developed by Apple Inc. exclusively for its hardware. It is the operating system that powers many of the company's mobile devices, including the iPhone; the term also includes the system software for iPads (predating iPadOS, which was introduced in 2019) as well as on the iPod Touch devices. It is the world's second-most widely installed mobile operating system, after Android.